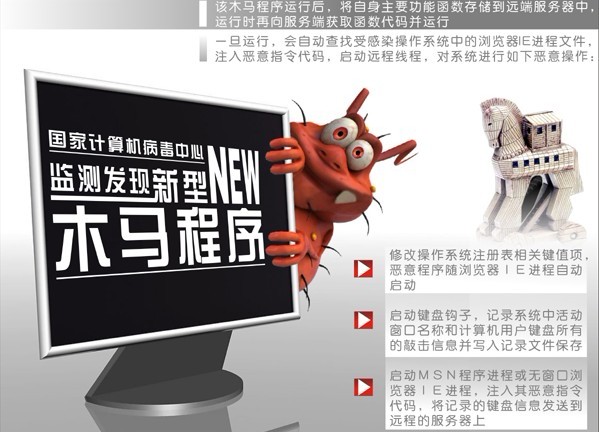
基本信息
中毒症狀:運行後在系統目錄system32衍生病毒檔案,並通過修改註冊表增加系統啟動項目達到開機啟動自身,從而
達到生成病毒檔案的目的。
成員舉例:病毒名稱: Trojan-Spy.Win32.Agent.pn
檔案 MD5: 90C9DEF19AB8A96484A12C65F697586F
檔案大小: 91928 bytes
感染系統: Win2000以上系統
對照命名: Trojan.Spy.Agent.DK
行為分析
1、一旦運行,該木馬複製自身到如下目錄,然後運行它的這些副本:
D:\myplay.pif
%System%\AlxRes061124.exe
%System%\scrsys061124.scr
副本運行後,會釋放如下檔案,然後運行它們。
%System%\winsys32_061124.dll
%System%\scrsys16_061124.scr
%System%\\winsys16_061124.dll
C:\myDelm.bat
myDelm.bat包含的內容如下:
:try
del "C:\Documents and Settings\Hunter\
桌面\Trojan-Spy.Win32.Agent.pn(90C9DEF19AB8A96484A12C65F697586F).exe"
if exist "C:\Documents and Settings\Hunter\
桌面\Trojan-Spy.Win32.Agent.pn(90C9DEF19AB8A96484A12C65F697586F).exe" goto try
del %0
該打包檔案的運行會導致原始樣本在運行後,被刪除,從而增加木馬的隱蔽性。
2、修改如下系統配置檔案。
winsys.ini [hitpop] test = 1
winsys.ini [hitpop] first = 1
d:\autorun.inf [autorun] open = d:\myplay.pif
winsys.ini [hitpop] ver = 061124
winsys.ini [exe] fn = C:\WINDOWS\system32\AlxRes061124.exe
winsys.ini [exe_bak] fn = C:\WINDOWS\system32\scrsys061124.scr
winsys.ini [dll_hitpop] fn = C:\WINDOWS\system32\winsys32_061124.dll
winsys.ini [dll_start_bak] fn = C:\WINDOWS\system32\scrsys16_061124.scr
winsys.ini [dll_start] fn = C:\WINDOWS\system32\winsys16_061124.dll
winsys.ini [hitpop] kv = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
"Userinit" = C:\WINDOWS\system32\userinit.exe,rundll32.exe C:\WINDOWS\system32\winsys16_061124.dll start
瑞星註冊表監控提示
主動防護 提示
主動防護 警告
主動防護 警報
主動防護 信息
Kaspersky Anti-Virus: 通知
5、連結網際網路,試圖下載如下檔案:
http://207.46.19.30/isapi/redir.dll?prd=ie&pver=6&ar=msnhome
http://208.172.13.254/
http://65.54.152.126/
http://69.108.159.61/library/dap.js
http://69.108.159.61/ads/6028/0000006028_000000000000000385411.swf?fd=www.msn.com&clickTAG=http%3A//g.msn.com/0AD00042/1023104.5.1%3F%3FPID%3D3505768%26amp%3BUIT%3DG%26amp%3BTargetID%3D1081844%26amp%3BAN%3D419629108%26amp%3BPG%3DMSNREC
http://69.108.159.61/br/hp/en-us/css/7/blu.css
http://69.108.159.61/br/hp/en-us/css/7/decoration/pipe.gif
http://69.108.159.61/br/hp/en-us/css/7/decoration/t.gif?http://stb.msn.com/i/BE/C7FA55CFA986A26FE1A325D0E2CC64.jpg
http://69.108.159.61/br/hp/en-us/css/7/decoration/t.gif?http://stb.msn.com/i/1D/E96930DEEF7EFDA819FBDC624BCBE.jpg
http://69.108.159.61/br/hp/en-us/css/7/decoration/msn_b.gif
http://69.108.159.61/br/hp/en-us/css/7/decoration/bullet.gif
http://69.108.159.61/br/hp/en-us/css/7/decoration/video.gif
http://69.108.159.61/br/hp/en-us/css/7/decoration/buttons.gif
http://207.46.216.62/c.gif?di=340&pi=7317&ps=83527&tp=http://www.msn.com/&rf=
http://207.46.216.55/c.gif?di=340&pi=7317&ps=83527&tp=http://www.msn.com/&rf=&RedC=c.msn.com&MXFR=9AD480265CF549E4BCE7D194DF92E5A5
http://63.150.153.30/br/om/js/1/s_code.js
http://207.46.216.62/c.gif?di=340&pi=7317&ps=83527&tp=http://www.msn.com/&rf=&MUID=9AD480265CF549E4BCE7D194DF92E5A5
http://128.241.21.149/b/ss/msnportalhome/1/H.1-pdv-2/s17852470343337?[AQB]&ndh=1&t=8/0/2007%204%3A28%3A6%201%20300&ns=msnportal&pageName=US%20Homepage%20V10.5&g=http%3A//www.msn.com/&cc=USD&ch=www.msn.com&server=msn.com&c1=Portal&c2=en-us&c3=10.5&c19=Dblu%2CW1%2CM5%2CF5%2CT5%2CE5%2CQ0&c22=False&c29=http%3A//www.msn.com/&s=1152x864&c=24&j=1.3&v=Y&k=Y&bw=792&bh=471&ct=lan&hp=N&[AQE]
http://65.54.194.118/ADSAdClient31.dll?GetSAd=&PG=MSN9TP&AP=1376
http://65.54.194.118/ADSAdClient31.dll?GetSAd=&PG=MSNREC&AP=1440
http://69.108.159.61/br/hp/en-us/css/7/decoration/WL.gif
http://69.108.159.61/br/hp/en-us/css/7/decoration/beta.gif
http://69.108.159.61/br/hp/en-us/css/7/decoration/search.gif
http://69.108.159.61/br/hp/en-us/css/7/decoration/msnbf.gif
http://69.108.159.61/br/hp/en-us/css/7/decoration/msft.gif
http://65.54.195.185/ADSAdClient31.dll?GetSAd=&PG=MSN9UT&AP=1339
http://65.54.195.185/ADSAdClient31.dll?GetSAd=&PG=MSNMMT&AP=1402
http://66.142.247.254/i/B2/B38AE443CC7154FB0B1FC2B5ACDA.JPG
http://66.142.247.254/i/91/94AB84A3A8C3441B39C4BFDF6885.jpg
http://66.142.247.254/i/AB/48246F6727DCA16791D0144BA78FA.jpg
http://66.142.247.254/i/F0/C71AF17271768EA57FE35F49CFF77.jpg
http://66.142.247.254/i/3A/E2E2E0FEA8E55AD59AAEBE43A7E246.jpg
http://66.142.247.254/i/50/C396B4EC11355010D2DF18C76E9F7D.jpg
http://66.142.247.254/i/31/DF78637BD438B9BB69A582FEA6879.jpg
http://66.142.247.254/i/AA/F78459FF8DDD39BF14DE4431D3395.JPG
http://66.142.247.254/i/56/F28E5AC0B9C07C5B1E13C6B797DC10.jpg
http://66.142.247.254/i/F2/C46FA12BAD98C59238B88C8417522.jpg
http://65.54.194.118/ADSAdClient31.dll?GetSAd=&PG=MSNCNT&AP=1463
http://65.54.194.118/ADSAdClient31.dll?GetSAd=&PG=MSNSUR&AP=1140
http://66.142.254.157/ads/764/0000000764_000000000000000385427.jpg
http://66.142.254.157/ads/1/0000000001_000000000000000017246.gif
http://69.108.159.61/as/wea3/i/en-US/saw/34.gif
http://69.108.159.61/as/wea3/i/en-US/saw/28.gif
http://69.108.159.61/as/wea3/i/en-US/saw/4.gif
http://69.108.159.61/br/hp/en-us/js/5/hpb.js
http://69.108.159.61/br/hp/en-us/js/5/ieminwidth.js
http://209.67.78.3/CNT/view/msnnkspc0020000003cnt/direct/01/
http://64.132.34.79/images/pixel.gif
試圖連結的IP為:
207.46.19.30
208.172.13.254
65.54.152.126
69.108.159.61
69.108.159.61
69.108.159.61
207.46.216.62
207.46.216.55
63.150.153.30
207.46.216.62
128.241.21.149
65.54.194.118
69.108.159.61
65.54.195.185
66.142.247.254
66.142.247.254
65.54.194.118
66.142.254.157
69.108.159.61
69.108.159.61
209.67.78.3
64.132.34.79
註:% System%是一個可變路徑。病毒通過查詢作業系統來決定當前System資料夾的位置。Windows2000/NT中默認的安裝路徑是C:\Winnt\System32,windows95/98/me中默認的安裝路徑是C:\Windows\System,windowsXP中默認的安裝路徑是C:\Windows\System32。
防毒方法:
2、在斷網的情況下,
關閉所有盤系統還原(右鍵
我的電腦,屬性,系統還原標籤頁,勾選在所有驅動器上關閉系統還原,確定.),
清空IE快取(右鍵IE圖示,屬性里,勾選清除所有脫機內容),
開機按F8進入安全模式,在安全模式下安裝
防毒軟體,並防毒